Sensitive data discovery tools for Apache Hbase
List of sensitive data discovery tools
In recent years many international organizations, countries, states etc. have introduced strict regulations regarding sensitive data storing and processing (GDPR in EU, CCPA in California state or PDBP in India just to name a few) to ensure that companies and organizations handle personal information correctly. This should motivate organizations to revise their data protection policies and identify all private data they collect and process. Invaluable help with this tedious task are sensitive data discovery tools.
Dataedo
Scan your databases and find and tag fields holding personal data so you can know what data you are processing and where to comply with data protection regulations such as GDPR or CCPA.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | HTML,MS Excel,PDF |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
Informatica Data Privacy Management
Informatica Data Privacy Management helps you discover, classify, analyze, protect, and monitor personal and sensitive data across your organization. In addition, it also lets you assess risk and monitor suspicious access to automate protection, transparency, and response.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | MS Excel,XML |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
BigID
BigID lets you find sensitive and critical data anywhere with transformative data discovery: combining next-gen ML cataloging, classification, cluster analysis, and correlation across all types of data.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
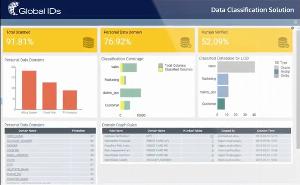
Global IDs
The Global IDs Enterprise Data Automation (EDA) platform comprises a set of core functions, i.e., automated sensitive data discovery, data profiling, data classification, data lineage, data quality, and more, thereby facilitating in compliance with regulations, such as GDPR and CCPA.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Discovering sensitive data can be done manually, simply by looking into each data source and identifying those with personal information inside. This solution, however, is very time-consuming and prone to mistakes. Much better is to use one of sensitive data discovery tools which does all that work automatically. Many of these solutions can work not only with structured, but also with semi-structured and unstructured data. Furthermore, some of them offer periodic synchronization with data sources, to automatically classify newly added information.
Why sensitive data classification is important? First and foremost, it is sign of care for clients and employees. No privacy data should leak, nor it should be seen by unauthorized people. Each organization should store only this information that are necessary for its’ functioning and collect them only with explicit consent (both are currently enforced by law). Not following rules can have severe consequences such as:
• Financial fines – London based pharmacy Doorstep Dispensaree Ltd was fined £275,000 for leaving medical files unprotected,
• Clients’ loss – PCI Pal conveyed a survey in which 83% of US customers claimed, they would stop spending with a business for several months in the immediate aftermath of a security breach,
• Legal prosecution – according to the Data Protection Act 2018 in UK, employee can face prosecution for data protection breaches,
• Loss of reputation – today’s more aware of cybersecurity customers may refuse to trust a company which violated data privacy rules.
Sensitive data discovery software is only part of personal information protection policy, although very important part. It is helpful especially when an organization uses many different data sources (files, databases, personal archives) or data regarding several countries, where identifying e.g., ID numbers may get complicated. However even small companies with clients from one region should be aware of private data in their systems, hence it is advised to frequently use one of listed sensitive data discovery software by organizations of any size.
 SQL Server
SQL Server
 Oracle
Oracle
 MySQL
MySQL
 PostgreSQL
PostgreSQL
 Amazon Redshift
Amazon Redshift
 Azure SQL Database
Azure SQL Database
 DBT
DBT
 Google Big Query
Google Big Query
 IBM DB2
IBM DB2
 MariaDB
MariaDB
 SAP HANA
SAP HANA
 Snowflake
Snowflake
 SQLite
SQLite
 Teradata
Teradata
 Vertica
Vertica