Sensitive data discovery tools
List of sensitive data discovery tools
In recent years many international organizations, countries, states etc. have introduced strict regulations regarding sensitive data storing and processing (GDPR in EU, CCPA in California state or PDBP in India just to name a few) to ensure that companies and organizations handle personal information correctly. This should motivate organizations to revise their data protection policies and identify all private data they collect and process. Invaluable help with this tedious task are sensitive data discovery tools.
Dataedo
Scan your databases and find and tag fields holding personal data so you can know what data you are processing and where to comply with data protection regulations such as GDPR or CCPA.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | HTML,MS Excel,PDF |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
1touch.io
1touch.io Inventa is an AI-based, sustainable data discovery and classification platform that provides automated, near real-time discovery, mapping, and cataloging of all sensitive data at enterprise scale. The platform assumes a zero-trust approach to data discovery and does not rely on input from organizational players. It automatically discovers, maps, and catalogs personal data in the enterprise network, using unique and proprietary network analytics.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Azure Information Protection
Microsoft’s Azure Information Protection (AIP) is a cloud-based solution that discovers, classifies, and protects sensitive organizational data by applying labels and encryption. Classification with Azure Information Protection is fully automatic, driven by users, or based on recommendation.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Avexta DataSense
Avexta DataSense search for sensitive PII data within your environment, perform real-time search, and analyze results, compliance, and risk management. In addition, it can identify file leaks in your network, and you can immediately start auditing trails to review access and policy.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
BigID
BigID lets you find sensitive and critical data anywhere with transformative data discovery: combining next-gen ML cataloging, classification, cluster analysis, and correlation across all types of data.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
BizDataX
BizDataX uses metadata inspection, data sampling, and various discovery rules, algorithms and heuristics to automate the process of locating sensitive data. Sensitive data discovery checks multiple systems, databases, hundreds or thousands of tables, and possibly billions of records.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
BOLT Data Discovery Tool
BOLT Data Discovery Tool helps you in identifying the exact locations where card data is getting stored and helps you in securing them. It helps in scanning all the major card brands including Visa, Mastercard, American Express, JCB, Discover, etc. You can also create your own RegEx to scan sensitive information pertaining to your business.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
ByteScout Sensitive Data Suite
ByteScout Sensitive Data Suite detects, removes, and analyzes your documents for sensitive data and personal identifiable information (PII). It analyzes and scans input documents (PDF, TIFF, scans, images) for potentially sensitive data or highlights sensitive data based on pre-defined policies/patterns based on selected sensitive data categories and creates a report with details about sensitive data categories and sensitive data stats.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
CA Data Content Discovery
CA Data Content Discovery helps you to find, classify, and secure business-critical data to reduce risk and simplify regulatory compliance. It finds where the data is located, classifies the data to determine sensitivity level, and provides comprehensive reporting on the scan results so that you can adequately protect data and mitigate exposure risks.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
ControlCase Data Discovery
ControlCase Data Discovery services help you to find and protect sensitive information quickly and cost effectively. It finds unencrypted data in any type of file across the whole network from one central location. CDD is not constrained by file types; rather it empowers to search the whole technical environment for sensitive data.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
Cyberhaven
Cyberhaven’s Data Detection and Response (DDR) platform transforms how you see your data and protect it from IP theft and insider threats. It automatically classify sensitive data based on data origin, its creator, and content. Find data even if you didn’t know where to look.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
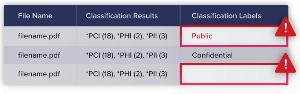
Varonis Data Classification Labels
Varonis Data Classification Labels automatically classifies sensitive data, even data that’s been encrypted by AIP, with our best-in-class scanning engine and applies persistent MIP labels. It easily identifies files that may have been mislabeled by users or that aren’t labeled at all by comparing MIP labels to Varonis classification results. Varonis can automatically fix labels in bulk, or you can manually reconcile them.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Varonis Data Security Platform
Varonis Data Security Platform is an all-in-one suite that lets you find, monitor, and protect sensitive data on-prem and in the cloud. It is an integrated platform where classification, access governance, and behavioral analytics combine to lock down data, stop threats, and take the pain out of compliance. It also lets you create custom rules to move, tag, archive, or delete data based on content type, age, access activity, and more.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
PKWARE
PKWARE’s PK Protect Platform automatically discovers, classifies, masks, and encrypts sensitive data, with no need for end-user intervention. It allows security teams and audit personnel to track critical information including which files are protected, where the files are stored, and which users have accessed them.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Mac OS,Windows |
| Structured Data: |
|
| Ustructured Data: |
|
DataSunrise
DataSunrise Database Security enables companies to pinpoint where sensitive data resides in all Databases and Data Warehouses, ensuring ongoing compliance and effective enforcement of monitoring and security policies. Intelligent automatic detection of relationships between tables when some of them contain sensitive PII or PHI data using Database Activity Monitoring, existing foreign keys, constraints in the table’s definition, and statistics about queries from the database.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
Discovering sensitive data can be done manually, simply by looking into each data source and identifying those with personal information inside. This solution, however, is very time-consuming and prone to mistakes. Much better is to use one of sensitive data discovery tools which does all that work automatically. Many of these solutions can work not only with structured, but also with semi-structured and unstructured data. Furthermore, some of them offer periodic synchronization with data sources, to automatically classify newly added information.
Why sensitive data classification is important? First and foremost, it is sign of care for clients and employees. No privacy data should leak, nor it should be seen by unauthorized people. Each organization should store only this information that are necessary for its’ functioning and collect them only with explicit consent (both are currently enforced by law). Not following rules can have severe consequences such as:
• Financial fines – London based pharmacy Doorstep Dispensaree Ltd was fined £275,000 for leaving medical files unprotected,
• Clients’ loss – PCI Pal conveyed a survey in which 83% of US customers claimed, they would stop spending with a business for several months in the immediate aftermath of a security breach,
• Legal prosecution – according to the Data Protection Act 2018 in UK, employee can face prosecution for data protection breaches,
• Loss of reputation – today’s more aware of cybersecurity customers may refuse to trust a company which violated data privacy rules.
Sensitive data discovery software is only part of personal information protection policy, although very important part. It is helpful especially when an organization uses many different data sources (files, databases, personal archives) or data regarding several countries, where identifying e.g., ID numbers may get complicated. However even small companies with clients from one region should be aware of private data in their systems, hence it is advised to frequently use one of listed sensitive data discovery software by organizations of any size.
 SQL Server
SQL Server
 Oracle
Oracle
 MySQL
MySQL
 PostgreSQL
PostgreSQL
 Amazon Redshift
Amazon Redshift
 Azure SQL Database
Azure SQL Database
 DBT
DBT
 Google Big Query
Google Big Query
 IBM DB2
IBM DB2
 MariaDB
MariaDB
 SAP HANA
SAP HANA
 Snowflake
Snowflake
 SQLite
SQLite
 Teradata
Teradata
 Vertica
Vertica