Sensitive data discovery tools
List of sensitive data discovery tools
In recent years many international organizations, countries, states etc. have introduced strict regulations regarding sensitive data storing and processing (GDPR in EU, CCPA in California state or PDBP in India just to name a few) to ensure that companies and organizations handle personal information correctly. This should motivate organizations to revise their data protection policies and identify all private data they collect and process. Invaluable help with this tedious task are sensitive data discovery tools.
Lumada Data Catalog
Lumada Data Catalog accelerates data discovery and metadata tagging to secure sensitive data, infer hidden relationships, and accelerate data self-service and insights.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus lets you find, classify, analyze, and track sensitive personal data, such as PII/ePHI, stored in file servers and SQL databases. Other key features include file access auditing, ROT analyzer, permissions analyzer, storage analyzer, and many more.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Mac OS,Windows |
| Structured Data: |
|
| Ustructured Data: |
|
McAfee DLP Discover
McAfee Data Loss Prevention (DLP) Discover lets you locate, classify, and protect your sensitive data both on-premises and in the cloud. Unified policy creation, reporting, and management give you better visibility and control over your most vital data. In addition, you can easily review and repair violations and prevent sensitive data from being proliferated outside of your environment.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | CSV |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
MENTIS
MENTIS leverages the power of Artificial Intelligence and Natural Language Processing to uncover sensitive data in the most complex of locations, be it structured, unstructured, Big Data, or on the Cloud. It ensures efficient identification of sensitive data with minimal false positives with a patented approach to data discovery.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Windows |
| Structured Data: |
|
| Ustructured Data: |
|
Velocity File Analysis Suite (FAS) Data Discovery
Micro Focus File Analysis Suite (FAS) Data Discovery lets you identifies and locates sensitive data and delivers increased visibility of unstructured data through AI-powered analytics. Analytics-based tagging, keywords, and data enrichment help create data subsets and refine data sets. This helps identify risk so you can act on data that needs to be managed (collect, hold, delete, declare as record).
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Micro Focus Secure Content Management Suite
Micro Focus Secure Content Management Suite discovers, protects, and manages your most sensitive data across its lifecycle. It lets you achieve greater visibility into your structured and unstructured data to uncover, manage, and encrypt sensitive information across your business applications and system databases.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Microsoft Information Protection and Governance
Information Protection and Governance in Microsoft 365 lets you accurately identify sensitive information across your enterprise with comprehensive classification capabilities, including machine learning. In addition, you can protect your sensitive data throughout its lifecycle by applying sensitivity labels linked to protection actions like encryption, access restrictions, visual markings, and more.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
MinerEye DataTracker
MinerEye DataTracker automates sensitive data discovery, mapping, indexing, and classification for security, privacy compliance, data minimization, and retention on-premise and in your cloud unstructured data. It handles the exponential
growth of insecure, unstructured data with actionable insights to meet compliance regulations and decrease cloud adoption costs.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | Linux,Windows |
| Structured Data: |
|
| Ustructured Data: |
|
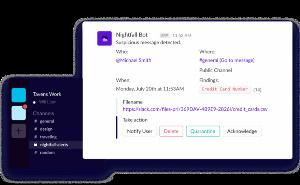
Nightfall
Nightfall is built to discover, classify, and protect data across any app. It uses machine learning to classify your sensitive data and PII with high accuracy. Nightfall takes a modern approach to cloud data protection, using machine learning to zero in on data that you deem critical – for easy, comprehensive coverage without the alert fatigue.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Northdoor Data Discovery and Classification
Northdoor’s Data Discovery and Classification (DDC) solution lets you automatically discover, classify, and protect sensitive data across environments. An easy-to-use, wizard-driven interface helps you drive classification forward quickly using the rules and policies of your business by providing your own definitions, keywords or data dictionaries, or by using any of the popular templated solutions including those for PCI, PHI, PII, Social Security Numbers, ITAR and other sensitive data types.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
PII Tools
PII Tools empowers you to scan your inventory and reveal any personal or sensitive data and analyze discovered data based on its severity, content, and context. In addition, you can report, delete, or quarantine suspect personal information and keep up with regulations with scheduled scans.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
PHEMI
PHEMI lets you tag, inventory, and control your sensitive data whether it’s in a file or buried in a relational table. It collects audit logs
concerning not only what changes were made to the system, but also data access patterns.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Privacy Request
Privacy Request automatically locates and categorizes personal data. It tracks the flow of data to, through, and from your company to ensure strict compliance and risk mitigation.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
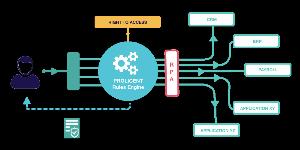
ProLicent
ProLicent is a powerful tool, which allows in a simple manner to identify the processing of personal data in your business and your eco-system. It is structured on the basis of a Data Privacy-driven rule engine, which assists the rapid and ready harnessing of all your personal data.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Proofpoint Data Discover
Proofpoint Data Discover finds and tracks sensitive information across your network with reliable, automated content analysis across on-premises file shares, SAN and NAS storage, and SharePoint sites. It automatically identifies sensitive data types most at risk to exposure, including PCI, PII, PHI, and GDPR. When sensitive information is at risk, you can visualize access rights, quarantine, or delete it automatically.
| Data Activity Monitoring: |
|
|---|---|
| Data Classification: |
|
| Encryption, blocking, masking and quarantining: |
|
| Export: | - |
| GDPR: |
|
| PHI (Protected Helath Information): |
|
| PII (Personal Identifiable Information): |
|
| Runs on: (for desktop): | - |
| Structured Data: |
|
| Ustructured Data: |
|
Discovering sensitive data can be done manually, simply by looking into each data source and identifying those with personal information inside. This solution, however, is very time-consuming and prone to mistakes. Much better is to use one of sensitive data discovery tools which does all that work automatically. Many of these solutions can work not only with structured, but also with semi-structured and unstructured data. Furthermore, some of them offer periodic synchronization with data sources, to automatically classify newly added information.
Why sensitive data classification is important? First and foremost, it is sign of care for clients and employees. No privacy data should leak, nor it should be seen by unauthorized people. Each organization should store only this information that are necessary for its’ functioning and collect them only with explicit consent (both are currently enforced by law). Not following rules can have severe consequences such as:
• Financial fines – London based pharmacy Doorstep Dispensaree Ltd was fined £275,000 for leaving medical files unprotected,
• Clients’ loss – PCI Pal conveyed a survey in which 83% of US customers claimed, they would stop spending with a business for several months in the immediate aftermath of a security breach,
• Legal prosecution – according to the Data Protection Act 2018 in UK, employee can face prosecution for data protection breaches,
• Loss of reputation – today’s more aware of cybersecurity customers may refuse to trust a company which violated data privacy rules.
Sensitive data discovery software is only part of personal information protection policy, although very important part. It is helpful especially when an organization uses many different data sources (files, databases, personal archives) or data regarding several countries, where identifying e.g., ID numbers may get complicated. However even small companies with clients from one region should be aware of private data in their systems, hence it is advised to frequently use one of listed sensitive data discovery software by organizations of any size.
 SQL Server
SQL Server
 Oracle
Oracle
 MySQL
MySQL
 PostgreSQL
PostgreSQL
 Amazon Redshift
Amazon Redshift
 Azure SQL Database
Azure SQL Database
 DBT
DBT
 Google Big Query
Google Big Query
 IBM DB2
IBM DB2
 MariaDB
MariaDB
 SAP HANA
SAP HANA
 Snowflake
Snowflake
 SQLite
SQLite
 Teradata
Teradata
 Vertica
Vertica